Maltek Solutions is an industry leading collaborative pentesting and vulnerability discovery services personalized towards your business needs. Greater value than leading competitors at half the cost
Consulting Services
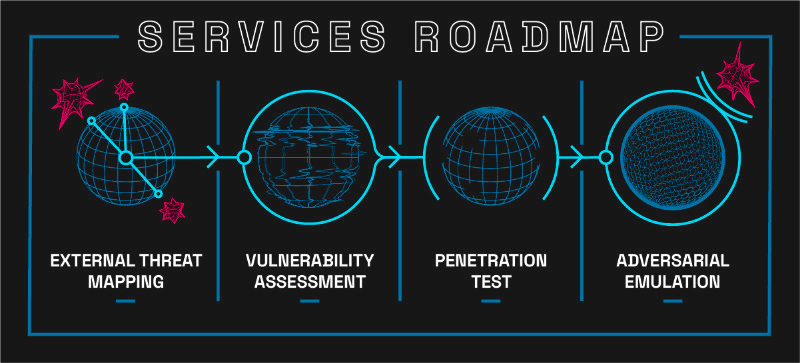
>> Start your security journey with a comprehensive security assessment.
EXTERNAL THREAT MAPPING
Many organizations face the challenge of securing an accurate picture of their organization from the outside. External Threat Mapping, also known as attack surface mapping, gives you a clear picture by identifying all potential targets of your organization that are externally facing.
VULNERABILITY ASSESSMENTS
Our low-cost rapid-delivery assessments are an excellent place to start your security journey
Vulnerability assessments can be performed on internal networks, external networks, and web applications. We use industry-standard scanning tools and techniques combined with our own proprietary data filtering process to provide you with the highest quality easy-to-understand results.
Other competitors deliver a massive stack of raw scan data and output. We do the filtering for you! We review every result, validate each finding, and organize the verified findings into a prioritized, concise, and actionable report.
>> Take the next step on the road to a secure infrastructure.
Penetration Testing
Maltek penetration tests cover the full range of a security incident. We work with you every step of the way to design and execute a simulated engagement, and then provide you with a complete breakdown of risk and impact.
Our comprehensive outside-in penetration testing services cover every threat category and are broken down into multiple categories:
External Penetration Testing
External tests focus on the means of entry into your internal network. All of your public-facing hosts, network services you provide, and public-facing network infrastructure are evaluated. Any potential means of entry is identified and assigned risk criteria.
Cloud Security Review
Don’t leave your business’ security solely in the hands of your cloud providers! Our cloud testing incorporates a review of Identity and Access Management (IAM) profiles, storage accounts, network security, logging and monitoring, and key management services that are critical to ensuring no unauthorized access results from your cloud infrastructure.
Web Application Testing
Web application tests utilize an OWASP-aligned methodology to comprehensively test your critical web applications for vulnerabilities that may be exploited to damage your business
Internal Penetration Testing
Internal tests focus on post-foothold activity. We simulate an attacker’s ability to exploit vulnerabilities, escalate privileges, and move laterally throughout the network.
Wireless Network Testing
Wireless tests evaluate your wireless networks by performing a comprehensive review that aligns with industry-leading practices.
We also ensure that critical assets are protected from users connected to guest networks by performing a rigorous segmentation verification analysis.
There’s no need to pay for travel! Our wireless testing is performed remotely via a pre-configured test appliance shipped to the locations that require testing.
Whether it’s legacy or development systems, or un-tracked services, our process of identifying these targets gives you the peace of mind that everything is properly accounted for.
CUSTOM SOLUTIONS
We do it all. Our in-house solutions and network of resources cover every domain of security infrastructure. Tell us what you need, and we will tailor a custom solution to fit your needs at a fraction of the cost you’ll see from other providers.

Training & Education
SECURITY AWARENESS TRAINING
>> The #1 risk to your organization is, was, and likely forever will be the members of the organization. In 2022, 98% of attacks included a social engineering component.
Our security awareness training services stand out from the rest. We connect with your workforce on a level that is easy to understand and effective. We clearly identify the most common means of attack, how your teams can identify these attacks, and how they should respond. With our training, your most vulnerable attack vector becomes your frontline of defense.
We can continue working with your organization to develop custom phishing email campaigns, physical security tests, and security response tracking. Watch as your team improves over time, improve your security, and build morale with our social engineering teambuilding exercises!
Custom Social Engineering Campaigns
We offer custom social engineering campaigns to help businesses test and improve their defenses against these types of attacks. Our team of experts will work with you to design and execute a tailored campaign that simulates a real-world attack which provides valuable insights into the effectiveness of your security measures. Through this exercise, you can identify vulnerabilities and take steps to remediate them, ultimately improving your organization's resilience against social engineering attacks. Contact us to learn more about how our custom social engineering campaigns can benefit your organization.
Engineering Services
>> Maltek Solutions can help build or automate your business needs. With a background in software development and cyber security, you can be sure that the solution is safe, secure, and reliable. Our software engineer services include:
Web Application development
Specializing in web development, Maltek Solutions can design, build, and deploy a full-stack application to fit your needs. Some common web applications include:
- Consumer-Facing Applications
- Business Logic Automation
- Data Aggregation & Visualization
Vulnerable Web Applications
Vulnerable Web Applications can evaluate potential employees, recruit new employees, train personnel, and more! With extensive experience operating Capture the Flag (CTF) and Cyber Security Competitions, our team can build the target app you always dreamed of – and tell you how to break it.
Infrastructure Automation
Managing Infrastructure can be a huge drain on IT and DevOps Teams. Infrastructure as Code (IaC) automates the deployment of new and existing infrastructure, making patches, redeployments, and test environments easier than ever. Maltek Solutions can codify your existing infrastructure or generate new Infrastructure as Code using the top IaC providers like HashiCorp and Ansible.
Modular Frameworks
Got a thing that needs to do a thing with other things? We got you. Modular frameworks allow an application to perform the necessary tasks while still allowing the end user to customize functionality as needed. Examples include plugin enabled:
- Incident Response Frameworks
- Vulnerable VM Generation Frameworks
- Command and Control Frameworks
Architecture Review
Our Architectural Review service helps businesses identify potential weaknesses and vulnerabilities in their technical systems. Our team will look at your setup and recommend improvements to enhance security. And if you need help implementing those recommendations, we've got you covered there too.
Custom Solutions
If you have a specific scenario that does not fit into the categories above, that’s okay! We can discuss your requirements and develop a custom engineered solution that is tailored to fit your needs.

Start taking measures to protect your assets.